The Building Blocks of Zero Trust Architecture
Time to read: 10 mins
To tighten IT security and protect US businesses against increasingly malicious cyber threats targeting ever-growing cloud-based computer systems, the drive to adopt a Zero Trust architecture is on the rise.
The key to successful cyber security is keeping malicious actors out, while maintaining business productivity, interoperability, and flexibility. Authorized users require secure access to networks from any location – whether that’s in offices, working remote outside the normal network boundaries, or connecting to regional hubs.
Organizations will need to invest effort and money to achieve Zero Trust, with Gartner predicting only 10% of enterprises would succeed in having Zero Trust plans in place by 2026. But you can’t simply buy Zero Trust, you need to build it from the ground up.
So how do you get started and what tools have you already got in place to help on your journey to a Zero Trust architecture?
So, what is Zero Trust?
First, let’s define Zero Trust, which is fast becoming a marketing slogan. It is best defined as a framework to secure a complex network comprising a blend of on-premises and cloud architectures from internal and external threats, particularly where many security incidents come from the misuse of user credentials.
Zero Trust relies on authentication, authorization, and validation to secure users’ access from inside and outside of the network, and this includes cloud-based connections and remote workers. It manages the permissions given to every device, the applications they can run and the data they can access, save, encrypt, and transport.
NIST, the authority on Zero Trust, defines seven key pillars. Those are as follows:
- All data sources and computing services are considered resources.
- All communication is secured regardless of network location.
- Access to individual enterprise resources is granted on a per-session basis.
- Access to resources is determined by dynamic policy.
- The enterprise monitors and measures the integrity and security posture of all owned and associated assets.
- All resource authentication and authorization are dynamic and strictly enforced before access is allowed.
- The enterprise collects as much information as possible about the current state of assets, network infrastructure, and communications and uses it to improve its security posture.
^From National Institute of Standards and Technology (NIST) Special Publication (SP) 800-207, Zero Trust Architecture, p. 6.
6 Tips for achieving Zero Trust
There is all-round acceptance that the perimeter-based approach to IT security is no longer enough, and a Zero Trust methodology will provide more effective protection.
This is evidently backed by the highest levels of US Government, with the Department of Defense (DoD) publishing its Zero Trust Strategy and Roadmap to achieve a Zero Trust architecture by 2027.
Studying how a leading military prioritises Zero Trust, can teach business a few conventional wisdoms about their own security practice.
Here are 6 guiding principles for reaching Zero Trust:
- Map your security goals and objectives to deadlines. In modern leadership, strategizing and plan-setting follows the 30, 60, 90 rule, which offers a very clear timescale for achieving goals. Albeit a short window of time, this creates urgency to reach security goals, and helps build momentum.
- Plan five years into the future. Any security plans should recognize the natural pace of technological change, adapting to new market trends and innovation to help combat existing and emergent threats. Those businesses that fall behind that competitive curve will face the challenges of legacy IT.
- Assign ownership. Even the most robust security controls and strategies cannot be operationalized in siloes. Train employees to approach security as a default mindset, because protecting a business is everyone’s responsibility.
- Recognise (and protect) the strategic value of data. Data should be accessible according to “least privilege” principles. Data may be ubiquitous, but its access must be tightly controlled.
- Commercial partners and supply chain partners must all be involved. The plan recognises that the growing number of commercial partners creates more opportunities for malicious actors to harm the department’s IT systems.
- Security isn’t only a technology problem. Zero Trust is not just a security model, it’s also a mindset. It requires a change of attitude, a new culture even, and this sifting view is more alerted to threats by removing costly assumptions about user trust.
Why is Zero Trust important right now?
Ask a security analyst about today’s most pervasive threats and the likely response will call attention to the groundswell of cybercrime activity. At a yearly rate, the volume and aggression of attacks is changing, forcing businesses to react, fortify, and review their security controls.

From state-sponsored threats to the evolution of ransomware, cybercrime stats make compelling, often alarming, headlines all the time. In 2023, for example, there been at least 300,000 malware incidents recorded daily. Worrying stats around the costs of a data breach can feel overwhelming, often causing seniority roles to lose sleep at night. IBM’s most recent report, illustrating an example of costly cybercrime, observed how during 2022 almost half (45%) of all breaches were cloud-based. Critical infrastructure breaches could cost upward of $4.82 million; the costs of a data breach, alarming, are relative to your industry.
Behind the stats, IBM was able to reveal a harsh reality about security strategies: the majority of organizations affected by a breach have no Zero Trust protocols in place.
Our security experts are engaged with clients around breach anxieties all-the-time, so we understand how shifting into the Zero Trust mindset isn’t an overnight switch. Tactically changing over to Zero Trust means having the right resources and skills, along with the best security products.
From the offset, there might be a misconception about reaching Zero Trust, where you have either tight compliance, a mixed estate, or both. But where Zero Trust doesn’t define any single product, you can accelerate alignment with new security models with fewer barriers.
Why identity is key?
Zero Trust continues to win mindshare across the security market, as enterprises rise to the challenge of a burgeoning cybercrime ‘industry’. Many analysts are starting to identity connections between breach occurrences and compromised privileged credentials. As a reported 80% of breaches target user credentials alone, a robust identity strategy should be high on the agenda.
Critically, identity is the next ‘new’ perimeter in a cloud-native world. In a rapid security market, where new products launch all the time (and some get sun-set), identity remains a rare constant. It’s a reliable convention that senior IT managers can turn to when layering in resilience.
A practical guide to Zero Trust
Tectrade simplifies Zero Trust by looking at 5 manageable ‘pillars’ that align with NIST’s framework, which includes:
- Identify
- Protect
- Detect
- Respond
- Recover
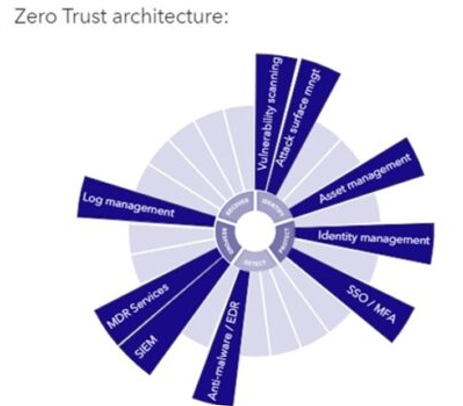
It’s important to remember that every stage in the model doesn’t capture a single tool; instead, each spoke can speak to multiple products, such as multi-factor authentication, identity protection, or even encryption.
Every spoke answers to a cornerstone piece of a wider security plan; a comprehensive security conversation would address every spoke individually, building (albeit gradually) toward a more refined Zero Trust ambition. A forensic view of security, one that views controls as granularly as this illustration, is more robust at keeping your data bolted against threat varieties.
Tectrade’s Head of Cyber Security, Leyton Jefferies, observes:
“It’s tempting to view security – and its many products, acronyms, and scares – as a daunting, unmountable task. But those anxieties will quickly melt away when a client starts to entertain a Zero Trust approach. Why? Because it removes many of the costly assumptions that criminals like to leverage for access. Think of Zero Trust fluidly enough, and you can picture a scenario where it wraps around the technology and managed services you already have. Start here; the next, natural step toward greater risk resilience is to identify gaps and start to close off new risks by onboarding beneficial products.”
How Tectrade simplifies cybersecurity
Reduce headache, rapidly unlock value, and get advice from accredited, security specialists – working with a Tectrade expert means finding a practical route into Zero Trust, using only the best the market has to offer for technologies and vendors.

We have even simplified a suite of products capable of improving your security posture through a Zero Trust approach, where every new layer will bring your business closer to a robust line of defence.
With such an influx of security products, navigating which new tools to onboard is often challenging. Tectrade’s security ‘bundles’ removes the complexity of purchasing multiple tools to complete key security competencies; instead, our security experts have already built the solutions you need, ready to deploy rapidly.
To find out more about Zero Trust, or whether you want to address your security concerns, review your existing posture, or understand more about our bundle offerings get in touch with our experts today.
About the author
Read more articles

Storage and Backup
A Buying Guide to Finding the Best Storage Solution for Your Business
Find the right storage solution for your company.
IBM Power
The IT Skills Gap Is Only Getting Wider in 2024
The IT skills gap is forecasted to widen in 2024 – especially for IBM i skills, what happens next?

About Tectrade
Tectrade Change Freeze (Dec-Jan)
We will be operating a ‘Change Freeze’ across our hosted and managed infrastructure to manage risk at this critical time.

